Transparent Data Encryption is by default configured for Azure SQL Database to use service managed key. This means that Azure is managing encryption keys for you with 90 days rotation. If you have some regulatory or data privacy requirement you can change the default setting and encrypt Azure SQL Database with your own key. I will show you how to set it all using the Azure Key Vault step-by-step in this tutorial.
The only one prerequisite you will need is configured Azure SQL Server. There is no need to have any database created because TDE is configured at server level and at database level you can only switch it on or off.
To use our own encryption keys we need to have Azure Key Vault preconfigured. If you haven’t done it till now, follow a few simple steps listed below.
Configure Azure Key Vault
Open Azure Portal and search for Key Vault item in available services. Click on the Create button and complete the form using your own Resource group name:
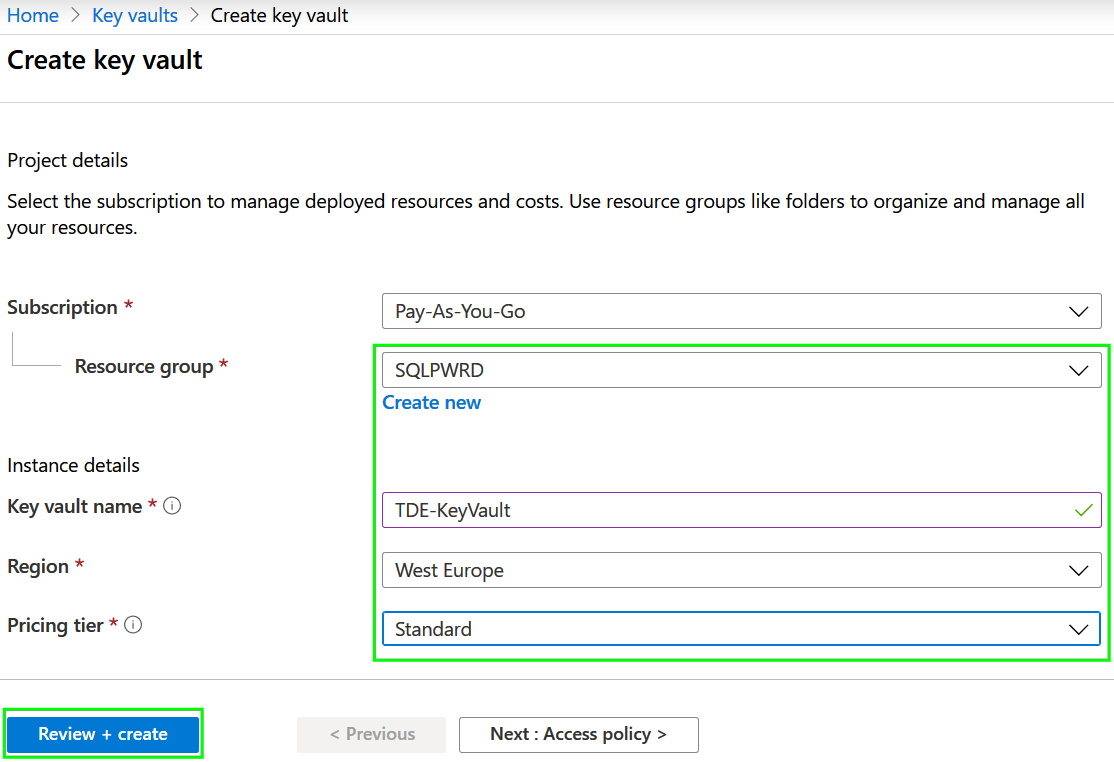
Press the Review + Create button and wait a few seconds before the deployment is completed.
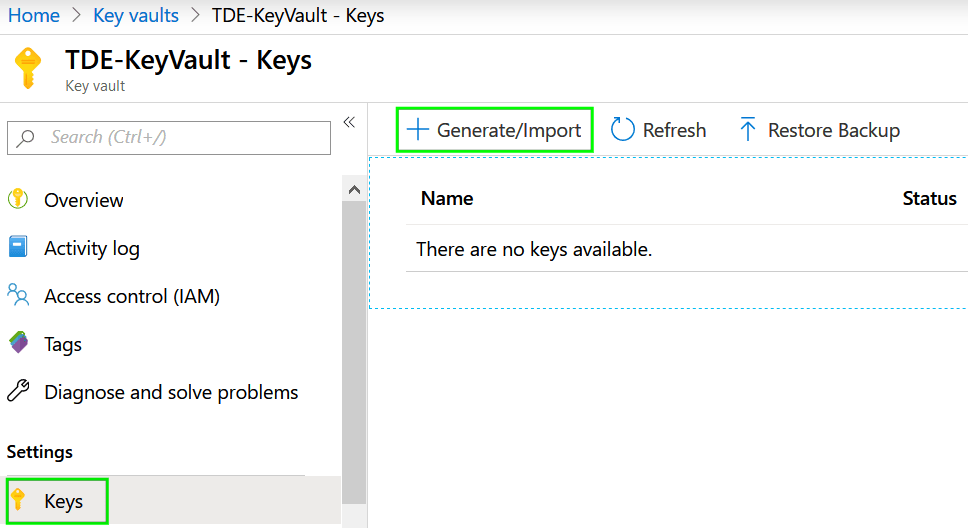
Create encryption key
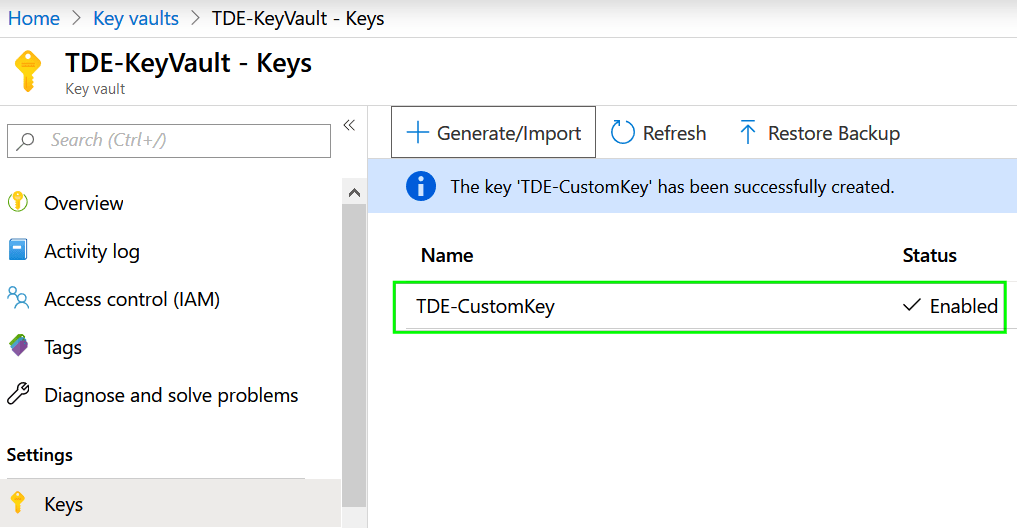
When the Key vault was successfully created we can create a new key that will be later used by for encryption by TDE service. Select for Keys item in the Settings section and Genera new one:
Name of the key is up to you. For other items, we will use default settings.
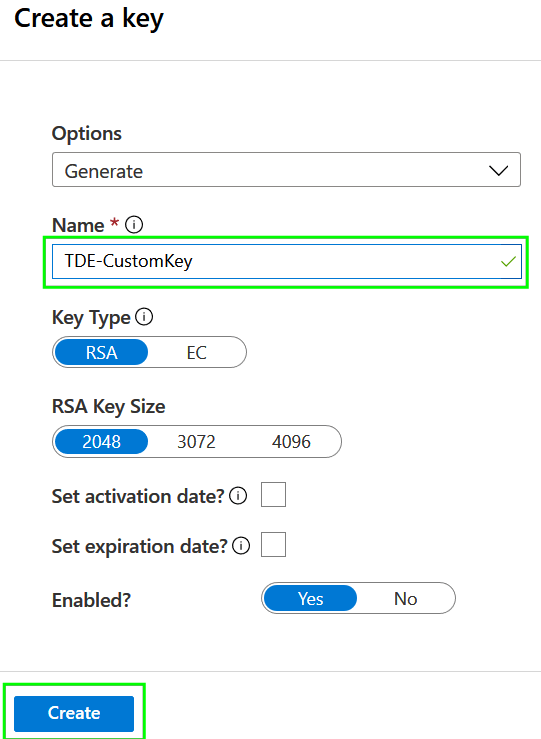
Press the Create button and verify that the creation of the key was completed:
Configure Transparent data encryption
Navigate to your SQL Server instance and in the Security group and click on Transparent data encryption item. As you can see using service-managed keys is the default option.

Because we will use for the encryption our own keys, change the setting to Yes and when prompted pickup you Azure Key Vault and select proper encryption Key:
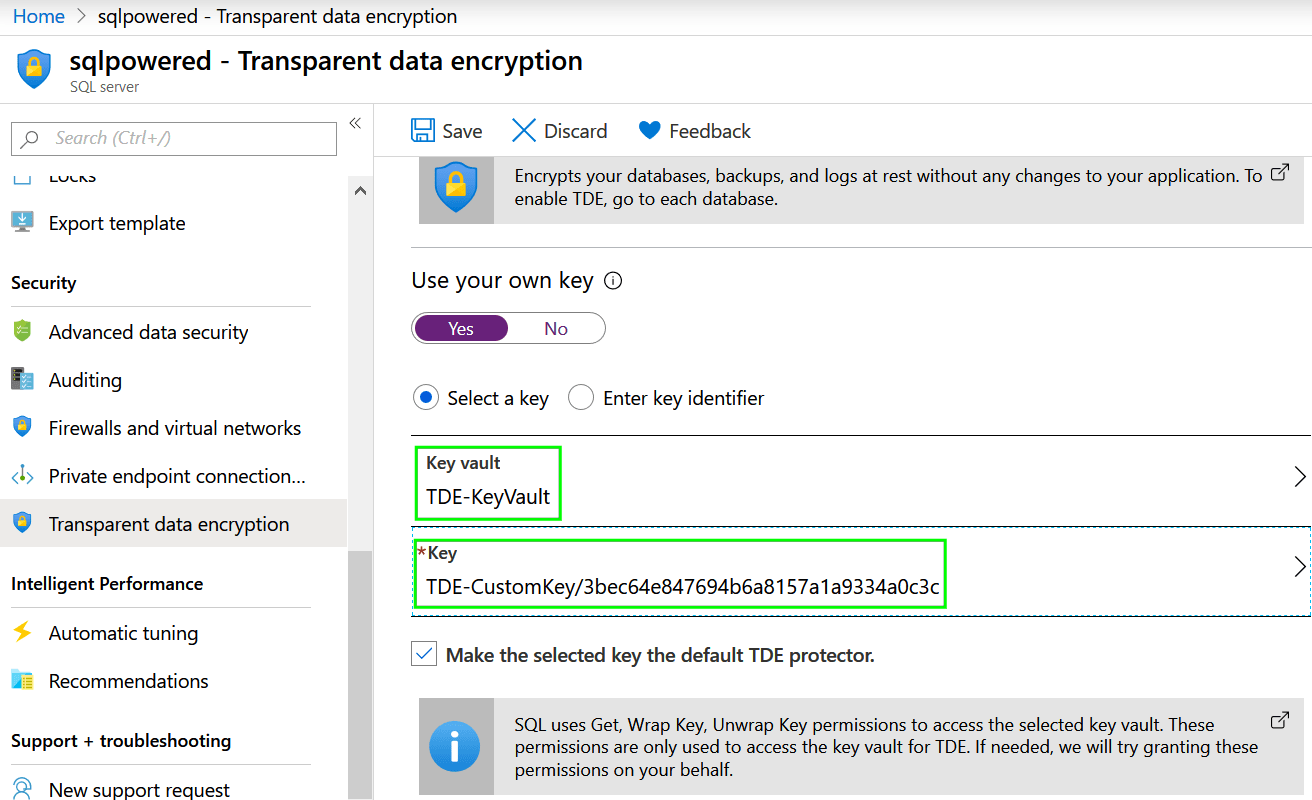
Finally, press the Save button.
If saving your new configuration has failed with following error, continue with next step:

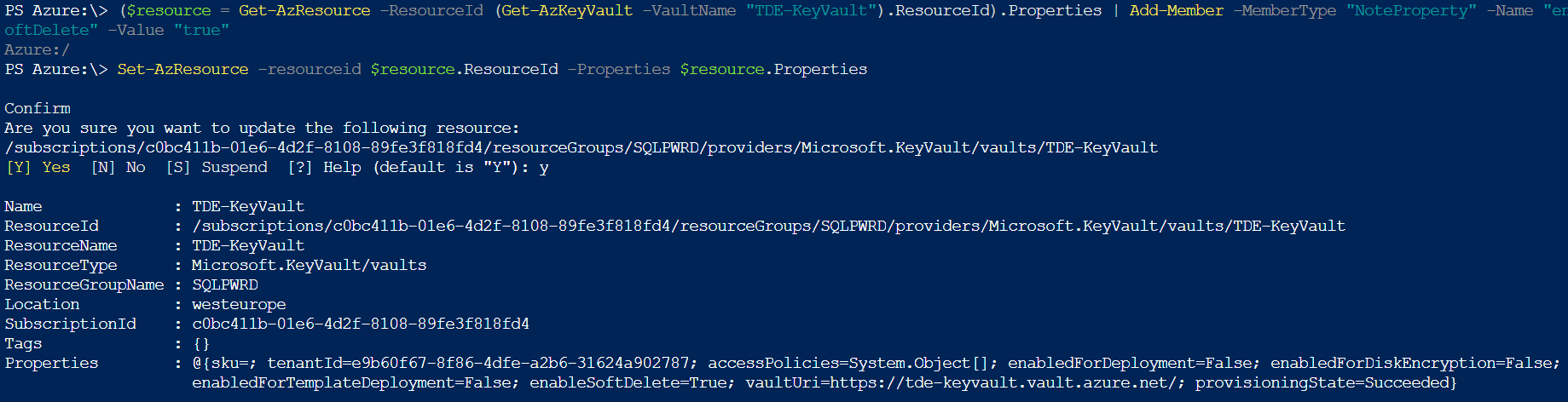
Using Azure Key Vault together with TDE requires the Key Vault to be properly configured. Soft delete functionality needs to be enabled to protect you against full data loss in case of accidental deletion of encryption keys. There is no such configuration option in Azure Portal and we will need to open Cloud Shell and configure the required setting using Powershell:
($resource = Get-AzResource -ResourceId (Get-AzKeyVault -VaultName "ContosoVault").ResourceId).Properties | Add-Member -MemberType "NoteProperty" -Name "enableSoftDelete" -Value "true" Set-AzResource -resourceid $resource.ResourceId -Properties $resource.Properties
Console output:
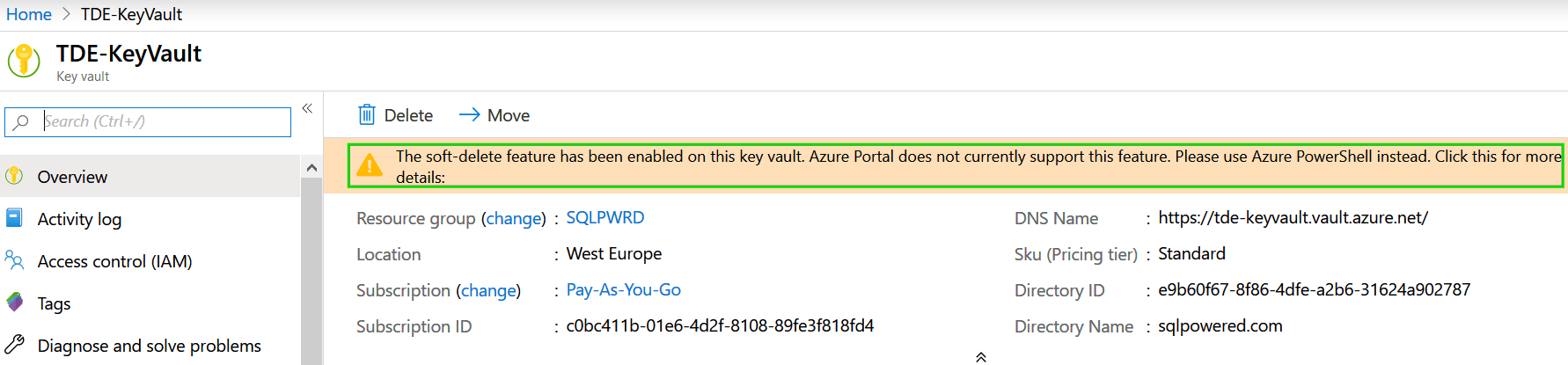
You can navigate back to Key Vault detail to check is the configuration succeed:
Let’s go back to TDE configuration screen and try again:

The operation completed successfully this time and our TDE is using our own keys stored in Azure Key Vault instead of service-managed keys.
